Just a month after 300,000 computers worldwide were affected by WannaCry, a new ransomware threat, called NotPetya is attacking government agencies and major private firms around the world.
Emerging news show that the attack began on Tuesday, with the first confirmed reports coming from Ukraine and Russia. Throughout the day, various companies from the United Kingdom, the United States, and across Europe and Asia also reported that their systems were hit.
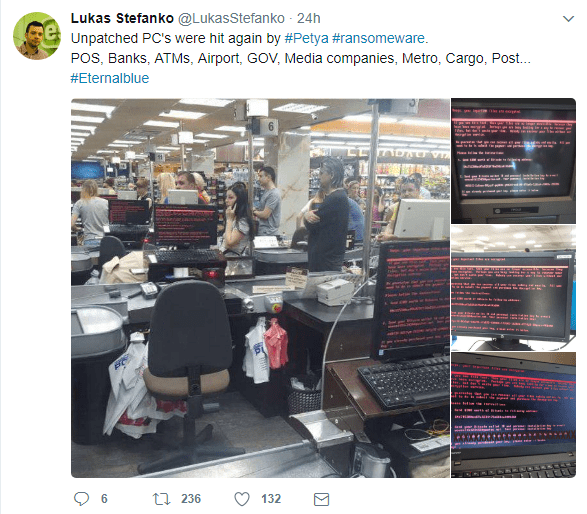
Researchers were eyeing a link to WannaCry, but security experts who investigated the attack stated it was an entirely new strain of ransomware after confirming the virus wasn’t a variant of the Petya ransomware. The malware is currently being nicknamed as “NotPetya”.
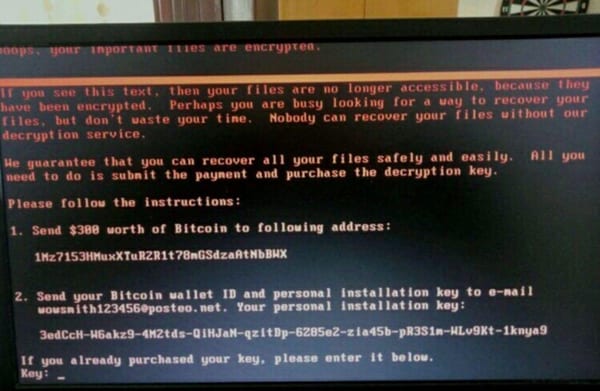
Based on the images posted on social media, the ransomware note is in English and warns computer users that their files have bee encrypted. If they want to regain control of their files, they have to pay a ransom of $300 for decryption services. The latest reports as of this writing state that about 20 transactions have already occurred (amounting to about $4,900 based on blockchain records). But there has been no news of any successful decryptions as of the moment.
NotPetya’s Main Target is Ukraine
Initial reports indicate that the majority of the attacks are happening in Ukraine. One of those greatly affected has been the Chernobyl nuclear power plant. It has switched to manual radiation monitoring services after having to shut down all of their Windows computers. The official website of the main Chernobyl plant has also been closed and there have been no reported radiation leaks. Systems at state-owned Ukrenego, Ukraine’s electricity supplier, have also been compromised. But according to a spokesperson, the ransomware threat has not affected the power supply.
Government agencies in the country weren’t spared, with officials reportedly sending images of their infected computers, including Ukrainian Deputy Prime Minister Pavlo Rozenko. The deputy prime minister said the government’s computer network went down. He also said the central bank reported disruption to operations at banks and firms. The municipal metro, state telecom, and Boryspil Airport in Kiev have also been affected.
Several private firms’ operations and systems have also been disrupted by the ransomware. Ukraine’s Channel 24 posted a screenshot of the ransom note. It read, “Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service.”
ATMs and point-of-sale terminals were also infected, with several people posting on social media about not being able to gas up and what appears to be stalled lines in a “Rost” supermarket.
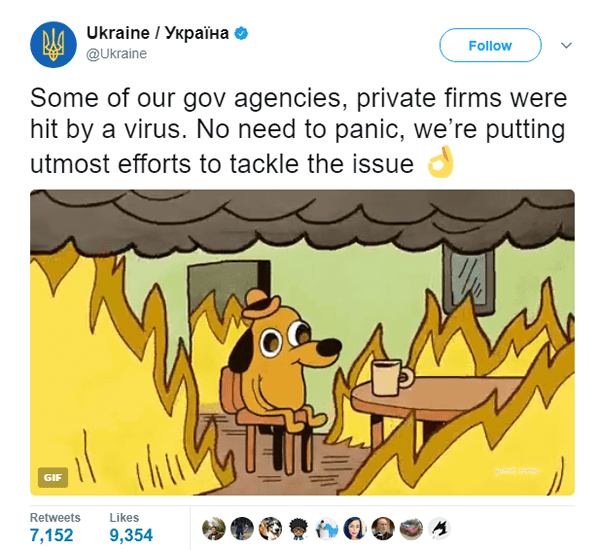
In general, the hack has disrupted the services and operations of airlines, banks, transportation, utilities, government, and retail in Ukraine. Despite the major impact of the virus, Ukraine has still been able to respond with some good humor in a public announcement a few hours after news of the attack broke out. The country’s official Twitter account posted a popular comic meme while requesting citizens not to panic.
Other Countries Affected by NotPetya
Based on reports, Russia is another country suffering major disruptions due to the NotPetya virus. The ransomware has spread to the partially government-owned oil giant Rosneft. The company said it was facing a “powerful hacker attack”. But even if its systems had suffered “serious consequences”, oil production was unaffected since it switched over to backup systems, according to Reuters.
Over at the United Kingdom, and British multinational advertising and PR company WPP has also reported that they had been targeted by the malware.
Danish shipping conglomerate Maersk confirmed the infection of systems across multiple sites, including at their freight forwarding company, Damco. Multinationals in Spain, companies in Lithuania, and a major shipping firm in the Netherlands have also been infected by the ransomware.
Other countries affected in Europe are France, Italy, Germany, and Poland.
Global law firm DLA Piper has also confirmed that several of its offices were infiltrated by hackers.
One of the three terminals in India’s largest container port, the Jawaharlal Nehru Port in Mumbai, was also affected by the attack. India-based offices of Reckitt Benckiser (owner of Lysol and Enfamil) and Beiersdorf (makers of Nivea products) reported some disruptions as well. While in Australia, the Hobart factory in Tasmania and a Cadbury factory were hit. There have also been attacks detected in some businesses across the Asia-Pacific region, but no further details have surfaced as of now.
In the United States, a hospital in Pittsburgh and the pharmaceutical company Merck were reportedly affected by the malware attack.
Is NotPetya the Same as WannaCry?
When reports of the virus first came out, most believed it was linked to the ransomware which hit hundreds of thousands of computers in April. Researchers stated that the new malware used the same EternalBlue exploit as WannaCry, which targeted a vulnerability in Microsoft Windows. Security experts believe this is why the virus has been able to spread so quickly.
Other security experts claimed the hackers could have borrowed a malware code used in the previous “GoldenEye” and “Petya” ransomware attacks.
However, it seems this latest strain of malware is even more dangerous than WannaCry and other predecessors since cyber security specialists believe it has no kill switch. Additionally, it has some added features in the malware which allows it to infect Windows computers that have already been patched for WannaCry. Aside from that, affected PCs are unable to reboot and are unresponsive.
Who is Responsible?
There is currently no report on the origins of the hack and who is responsible for it. But since the present threat has affected Ukraine’s electricity service, some are speculating that it could have been Russia. The country was blamed for attacks on Ukraine’s power grid in 2015 and 2016. However, Russia has denied all cyber attacks on foreign soil.
The Seriousness of Ransomware
After last month’s WannaCry scare, security experts and governments urged companies and consumers to update their computers with a Microsoft patch as protection from the virus. However, the quick spread of the new ransomware leaves one to assume that not too many took the malware threat seriously and/or failed to secure their PCs. On the other hand, this can indicate that hackers are getting better at their “job”.
In any case, everyone is advised to take protective measures to prevent ransomware and other viruses from infecting their computers.


