No matter how safe you are online, you can still be the victim of cyberstalking, identity theft, and security breaches. Thankfully, there are VPN services that can help protect you from hackers and other malicious actors.
What is a VPN?
A VPN (virtual private network) redirects your internet traffic through a specialized remote server that hides your IP address and encrypts your data. By extending your private network over your public internet connection, a VPN hides your browsing activity and protects your data from hackers.
How Does a VPN Work?
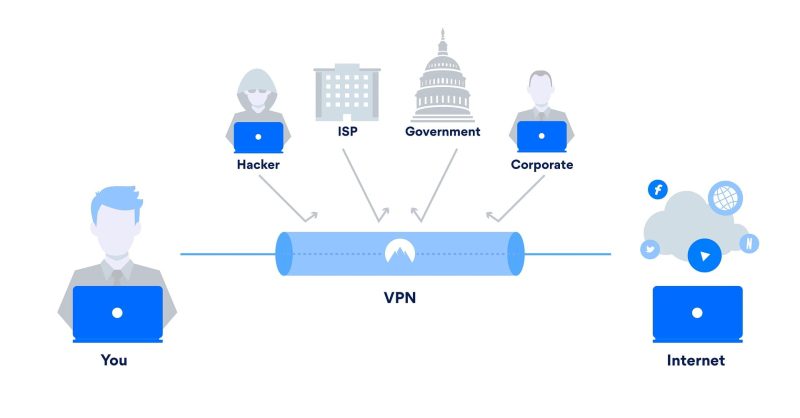
A virtual private network protects your connection and all data that passes through that connection in three layers:
1st layer → Encryption. Before anything else, your VPN encrypts your data (or converts all the information into a code that can’t be unencrypted without a matching key). So even if an unauthorized person manages to get ahold of your data, they still won’t be able to understand it.
2nd layer → Tunneling Protocol. Your VPN then establishes a direct connection between your computer and a VPN server. This private “tunnel” secures your connection over the public internet.
3rd layer → Authentication. Only users with the right authentication keys can access the tunnel and the VPN server. This is also the protocol that un-encrypts your data after it reaches its destination.
So, a virtual private network encrypts all the data that you are sending or receiving via your internet connection. Then it establishes a secure “tunnel” connection to a VPN server by using authentication keys. Once the connection is established, your computer then connects to the internet using that secure tunnel connection, and all your activities become private.
Why Do You Need a VPN and How Does it Benefit You?

Initially, virtual private networks were designed for businesses, big corporations, or governments with offices in different physical locations. VPNs enabled these groups to safely communicate over the internet and exchange sensitive information between their offices.
But a virtual private network isn’t just for people who have a business to safeguard or think they have anything to hide.
You may not be aware of it, but while you’re surfing the net, hackers are trying to steal your personal data. Even something as innocent as your shopping history can be quite a goldmine for unscrupulous online marketers. In fact, with the increasing popularity of mobile devices, hackers are starting to target mobile users and websites.
According to Forbes, data is the new currency of the digital age. And much like other currencies in the world, many people want to get their hands on it. Congress has even allowed your internet service provider (ISP) to mine and sell your data.
With a virtual private network, you will be safe from hackers, governments, and black hat marketers. That’s why regular internet users should consider using VPN technology to secure their internet connections.
The Benefits of a VPN
- A VPN protects your precious data from hackers while you’re connected.
- It conceals your physical location from snooping advertisers, governments, and all kinds of stalkers.
- VPNs unlock the geo-restriction in your country so you can access a wider range of content.
- And it lends you some anonymity on the internet.
What is a VPN Kill Switch?
On top of the tunnel protocol and encryption, there’s also this thing called a VPN kill switch. As its name clearly suggests, a VPN kill switch is a feature that automatically stops your internet connection whenever your virtual private network fails. This way, you won’t unknowingly surf the internet uncloaked. It’s sort of like a circuit breaker for your internet connection. However, not all VPN services have built-in kill switches.
Now, this is just the simplest explanation for how a virtual private network works. The more computers, connections, and servers involved, the more intricate the actual VPN framework is.
What are the Types of VPN?
Remote-access VPN
This type of VPN enables an individual user to establish a connection to a private computer network (like your business’ network) from a remote location. In order for this to work, there are two basic components called the network access server (NAS) and the client software.
The client software is an application that has to be installed on the user’s computer. It sets up the tunnel connection from an individual computer to the VPN server.
The network access server (a.k.a. the media gateway) is where individual computers connect to, via the internet, in order to connect to a VPN. It can either be a dedicated server or an application running on a shared server. But, before a connection can be established, the NAS has to authenticate that the user has valid credentials (username and password).
Site-to-Site VPN
This VPN is similar to a remote-access VPN, but on a much larger and more complex scale. Instead of individual computers connecting to a VPN server, it establishes a secure private connection between two or more networks of computers that are in different geographical locations. And instead of a VPN server, each network is secured with a VPN gateway, which is like a digital gate in the network tunnel
This type of VPN is most often used by companies or organizations that have offices in multiple cities or countries. It establishes a secure connection between different physical offices.
For example, a company has offices in New York, Paris, and London, and each office has several employees, each with their own computer. In every office, all the computers are connected via a local area network (LAN). These networks are connected to each other via a VPN server. In most cases, each LAN has its own VPN gateway that encrypts the data before sending it through the digital wilderness.
What are the Different VPN Security Protocols?
Now, the two types of VPNs mentioned above may use different security protocols. A VPN protocol is a set of rules that computers follow to establish a tunnel connection to VPN servers. And each VPN protocol has its own features and levels of protection. Below are some of the popular types of VPN protocols used today:
Internet Protocol Security (IPSec)
The most common VPN protocol, it secures your internet protocol communications by authenticating your connection and encrypts all data that passes through that connection.
Layer 2 Tunneling Protocol (L2TP)
Usually, this is used in tandem with IPsec. The L2TP establishes a secure communication tunnel between two L2TP connection points. While IPsec deals with the tunnel security, data integrity checks, and encryption to make sure the tunnel is secure, and that the data packets arrive at their destinations safely.
Point-to-Point Tunneling Protocol (PPTP)
One of the oldest and most widely used security protocols around, it can be installed on most existing operating systems today. However, like the L2TP, it only establishes the tunnel connection. It still needs another protocol, such as Generic Routing Protocol (GRE) or Transmission Control Protocol (TCP) to handle data encryption.
Secure Sockets Layer (SSL) or Transport Layer Security (TLS)
SSL, or its newer version TLS, is for web browsers to enable users to authenticate internet sessions, create secure connections, and exchange encryption keys without the need for installing a client software. These two protocols are often used by online shops that take credit cards or other sensitive data.
Secure Shell (SSH)
This network protocol provides strong authentication and creates an encrypted connection between a secure shell client and a remote server. Data itself is not encrypted, but the tunnel connection where data flows is. Aside from data, it can also transmit commands to a remote computer.
It pays to be a little bit cautious sometimes, especially when you value your privacy and the security of your personal data.
If you want to know which virtual private network service you should get for your home computer or mobile devices, check out our review on the best VPNs available today.


