We all know how much computers and the internet help improve our lives. We can now be more productive, communicate easily, and have endless entertainment options. Unfortunately, nothing is ever perfect. Negative effects come with the positive benefits of digital technology. Those hours you spend using your computer and browsing the web daily can make you vulnerable to a wide range of digital threats. These include viruses, phishing attacks, ransomware, hacking, identity theft, and more.
Thankfully, we do have excellent antivirus software choices these days, and most computer systems have built-in firewalls and security protocols to give us a reliable enough level of protection. Still, there might be some threats that will escape your notice. It is highly important to be aware of them and know what safety measures to take.
Malicious Individuals Snooping on Your Wi-Fi
Your private Wi-Fi network at home affords you a high level of security. But the moment you log into networks in cafes, airports, or hotels, your vulnerability increases. The risk of running into a WI-Fi eavesdropper is high. On many occasions, the snooper can just be sitting over at the next table, or beside you at the airport.

They can then monitor any sensitive information that you send out to the web without your knowledge unless you protect yourself properly. To ensure that you do not fall victim to snoopers (who are most likely identity thieves, hackers, or scammers), here are some safety measures you can implement:
- When opening websites, check if the URL has “https://” If one doesn’t, then that page is unsafe and you should get out of there pronto. Also, if you come across unsecured pages asking you to log in using your email or social media account, exit immediately. Those websites are most likely phishing pages and can only mean trouble.
- Make use of a Virtual Private Network or VPN to mask your online activities. There are many reliable VPN choices, including CyberGhost, IPVanish, and AirVPN.
- Enable extra protection for your often-used email and social media accounts. You can activate two-factor authentication, for example, to add another layer of security. Make use of strong security questions as well, especially for password changes. This way, unauthorized individuals will have a tough time locking you out of your own accounts.
- Keep all of your computer software updated. Old versions are likely to have codes that can be exploited by hackers to create a backdoor entry to your system. So, be diligent in updating crucial software. You can automate this process for convenience.
- If you have to do online banking, change your passwords, or fill up important forms – it is best to do these activities when you are on a secure network.
Harmful Programs Transmitted by USB Drives
One of the most overlooked security threats is a USB drive. Maybe a friend borrowed your thumb drive in a pinch. Unknowingly, he infected it with a virus. Then, when you plug it into your system, you unwittingly corrupt your computer as well. Not good.

Although most computers these days are equipped with warning systems that will inform you if a USB device contains a malware, they are not capable of defending you from all threats. These tips will improve your protection:
- Exercise caution and don’t give in to curiosity. There are stories going around of people unexpectedly receiving a malware-infected USB stick in the mail. These people willingly plugged the device into the computer, just to find out what’s inside. Needless to say, their systems were infected by the virus. So, be extra careful and don’t plug any suspicious USB device to your computer.
- Install an antivirus software that has a USB drive protection feature. If you have one already, double check the settings and make sure this feature is activated.
- Even if you have automatic USB protection built into your computer or via an antivirus package, make it a habit to thoroughly scan the device just after plugging it in. Don’t open anything in it until after the scan has concluded.
- Minimize usage of USB sticks. Save or share your data in the cloud instead. Of course, implement necessary cloud protection as well.
Someone Peeking at You through Your Webcam
Some stalkers can monitor you in your private space during your private time through your webcam. Unfortunately, it is not like we can totally get rid of webcams since we need them to communicate with people we care about who are far away. So, what to do?

- When you are not using it, keep the webcam covered. You can tape over it, or if it has a shutter, then use that.
- For Windows users, you can access the “Device Manager” menu from the Start button. Select the “Webcam” option located in the “Imaging devices” section. Then, click “Disable.” You can enable it again when you’re going to use it.
- For MacOS users, disabling the webcam is, unfortunately, harder. You can back up your system files first, and then go to the folder with the “Macintosh HD/ System/ Library/ Quicktime” address, and then remove the file named QuickTimeUSBVDCDigitizer.component
- Another good solution is to carefully select which applications in your computer can use the webcam or not.
- If your webcam is attached to your computer via USB, then simply pull it out when not in use.
Scams Masquerading as Real-Looking Messages
Just recently, a highly potent phishing attack targeted Gmail users. Many fell victim because the phishing page looked so much like the real Gmail login page. People who are in a hurry or are not vigilant enough will easily miss the fact that the page is dangerous.
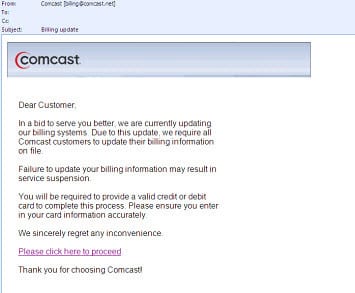
This is just one of the many examples of dangerous pages and messages circulating on the internet today, all of which are meant to fool people into giving up personal details and other sensitive data. Protect yourself:
- If you notice that your email or a webpage you often visit is behaving suspiciously, exercise caution no matter how minor your suspicion is. For example, the logo of your online banking page looks off somehow, or perhaps you just logged into your email yet this attachment you clicked on asked you to log in again. Things like these often mean there is something fishy going on.
- When you do find something suspicious, check the URL first and find the https:// or green lock key. If you don’t find that, then exit/close the page right away.
- Be careful opening email attachments. If you see that it is a PDF or JPEG file, but it opens as a webpage, then that is likely a virus or a phishing attack. Close that immediately, and then run a complete malware scan.
- Stay clear of pop-ups, especially those saying you won something, or that there is a virus and you need to install something to get rid of it. If you are really worried about a malware, go to your antivirus software and run a scan from there.
- Keep computer applications up to date, including browsers and email apps.
Conclusion
By being aware of these often-overlooked digital threats, you are one step closer to keeping yourself and your computer safe. Also, always remember that vigilance will go a long way towards protecting yourself while using your computer and the internet. Make sure as well that your system is fully equipped with defensive solutions to minimize harmful programs from infecting your machine.


